Security & Compliance Services
When it comes to compliance, we've got the experience. NerdSquad offers custom cybersecurity and compliance solutions utilizing the most advanced and reputable software providers in their respective industries.

DNS Filtering & Employee Monitoring
Block malicious websites and filter harmful or inappropriate content. However, it goes above and beyond simple website filtering. Ensure that company data remains secure and control what employees can access on company-managed devices and networks. Take it to the next level with advanced employee productivity and monitoring for remote workforces and high security / compliance environments.
Communications Encryption & Full Data Archiving
Encrypt all or some sensitive email communications. Archive all sources of data including email, SMS messages, all cloud services, social media, website versions, marketing collateral and more for easy eDiscovery and audit compliance when the need arises. We utilize the most secure and standardized service providers for easy integration with your industry specific applications.


Phishing Simulation and Security Awareness Training
Automatically send random simulated phishing emails to test employees' ability to identify malicious content. Conduct regular courses on the latest security trends and document employees' completion as required by many security standards. The weakest points on an organization's "attack surface" are human, not machine. Constant monitoring of your systems plus protection from risky behavior is integral to our multi-layered protection strategy.
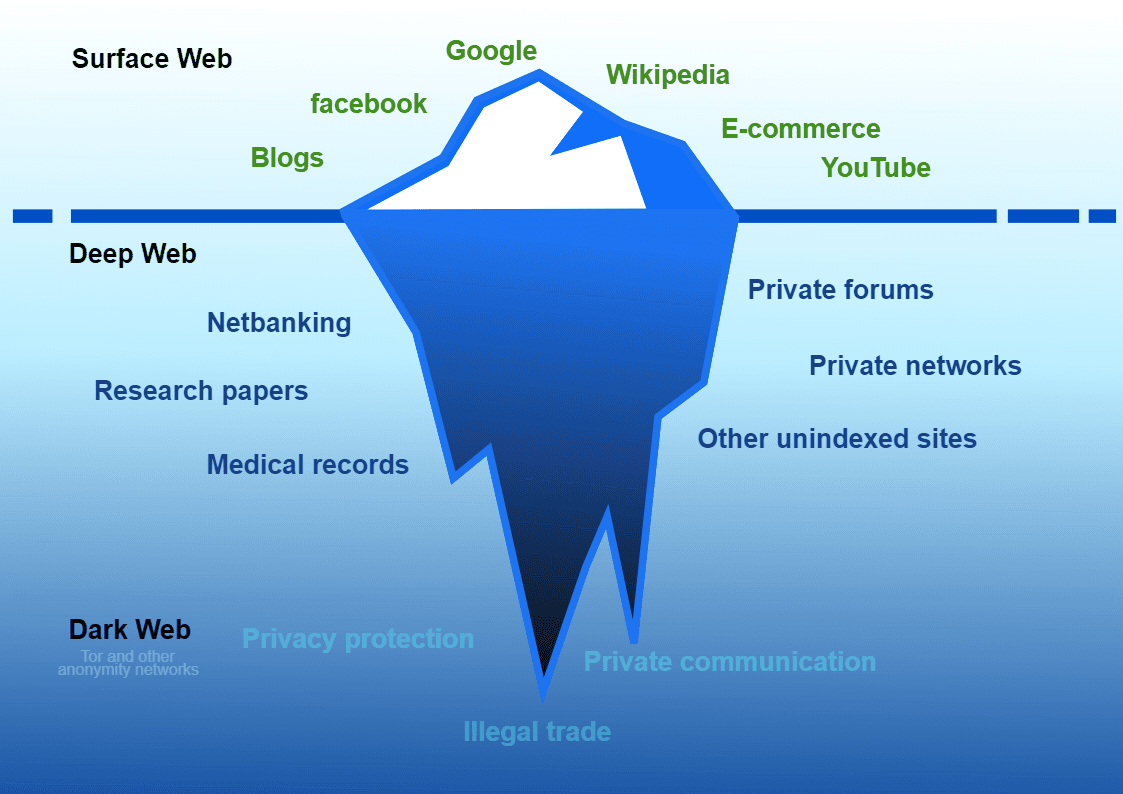
Dark Web Monitoring
Sophisticated analyst-validated dark web intelligence combined with cutting-edge live search capabilities enable you to identify compromised or stolen data and close security gaps fast. We can deliver actionable intelligence that empowers you to proactively protect your data from the risk of a devastating security breach. We won't just tell you you're at risk, we'll show you.

Penetration Testing
Periodic penetration tests of your entire technology stack to identify exploitable weaknesses is crucial for businesses that manage sensitive information. These tests include highly technical tactics designed to test both internal and external exploits. We will review the results of these tests with stakeholders and make recommendations to remediate those vulnerabilities. Regular pen-testing is required by organizations that must adhere to the strictest of data security standards.
Cybersecurity Insurance
Once the requisite protective systems have been implemented, your organization may be eligible for cybersecurity insurance. This covers the costs of addressing the breach, legal expenses, recovering lost funds from unauthorized transfers, ransoms, investigations and the costs incurred by small businesses to implement recovery measures to get back on track. This typically goes farther than what is included in general liability policies.


